Posted by: Pdfprep
Post Date: November 23, 2020
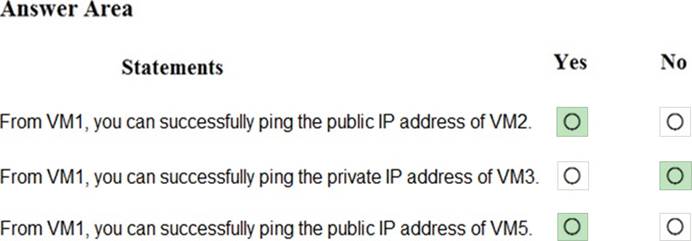
HOTSPOT
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No . NOTE: Each correct selection is worth one point.
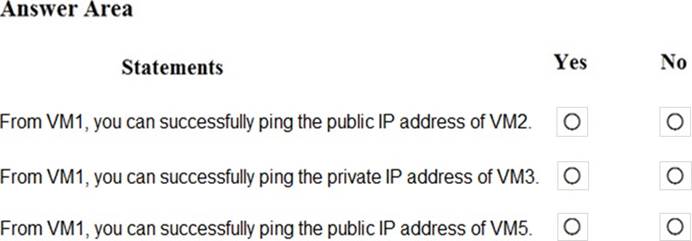
Answer: