Refer to the exhibit.
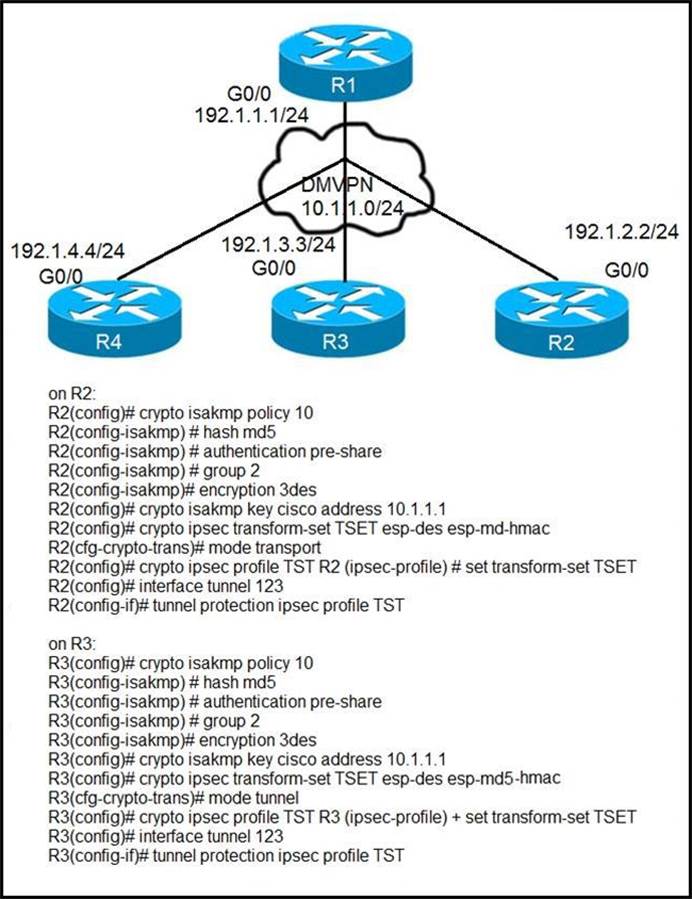
After applying IPsec, the engineer observed that the DMVPN tunnel went down, and both spoke-to-spoke and hub were not establishing.
Which two actions resolve the issue? (Choose two.)
A . Change the mode from mode tunnel to mode transport on R3.
B . Remove the crypto isakmp key cisco address 10.1.1.1 on R2 and R3.
C . Configure the crypto isakmp key cisco address 192.1.1.1 on R2 and R3.
D . Configure the crypto isakmp key cisco address 0. 0. 0. 0 on R2 and R3.
E . Change the mode from mode transport to mode tunnel on R2.
Answer: AD
Explanation:
The first six commands are used to configure IPSec Phase 1(ISAKMP Policy).
Here is the details of each command used above:
+ crypto isakmp policy 10-This command creates ISAKMP policy number 10. You can create multiple policies, for example 7, 8, 9 with different configuration. Routers participating in Phase 1 negotiation tries to match a ISAKMP policy matching against the list of policies one by one. If any policy is matched, the IPSec negotiation moves to Phase 2
+ hash md 5-MD 5 algorithm will be used
+ authentication pre-share-Authentication method is pre-shared key.
+ group 2-Diffie-Hellman group to be used is group 2
+ encryption 3des-3DES encryption algorithm will be used for Phase 1.
+ crypto isakmp key cisco address 10.1.1.1-The Phase 1 password is cisco and remote peer IP
address is 10.1.1.1
The next two command lines are used to configure IPSec Phase 2(Transform Set)
+ crypto IPSec transform-set<transform-set-name>-Creates transform-set called<transform-
set-name>
+ esp-des-ESP IPSec protocol with the 56-bit Data Encryption Standard(DES) encryption
algorithm will be used
+ esp-md 5-hmac-ESP with the MD 5(HMAC variant) authentication algorithm will be used.
+mode transport: only encrypts the payload and ESP trailer
or
+ mode tunnel: encrypts the IP header of the ENTIRE packet