Posted by: Pdfprep
Post Date: November 21, 2020
A security consultant is trying to attack a device with a previously identified user account.
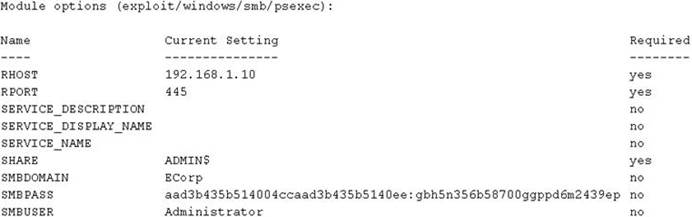
Which of the following types of attacks is being executed?
A . Credential dump attack
B . DLL injection attack
C . Reverse shell attack
D . Pass the hash attack
Answer: D
