Posted by: Pdfprep
Post Date: November 22, 2020
An analyst is currently looking at the following output:
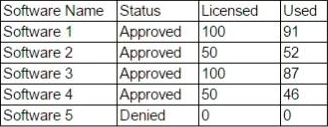
Which of the following security issues has been discovered based on the output?
A . Insider threat
B . License compliance violation
C . Unauthorized software
D . Misconfigured admin permissions
Answer: B
