Posted by: Pdfprep
Post Date: October 26, 2020
A hacker issued a command and received the following response:
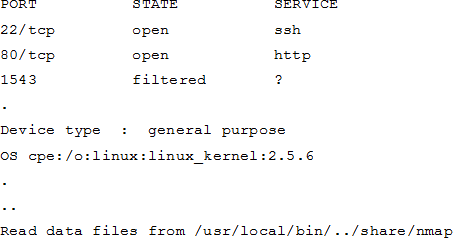
Which of the following describes what the hacker is attempting?
A . Penetrating the system
B . Performing a zombie scan
C . OS fingerprinting
D . Topology discovery
Answer: A
