The Chief Information Security Officer (CISO) has asked the security analyst to examine abnormally high processor utilization on a key server.
The output below is from the company’s research and development (R&D) server.
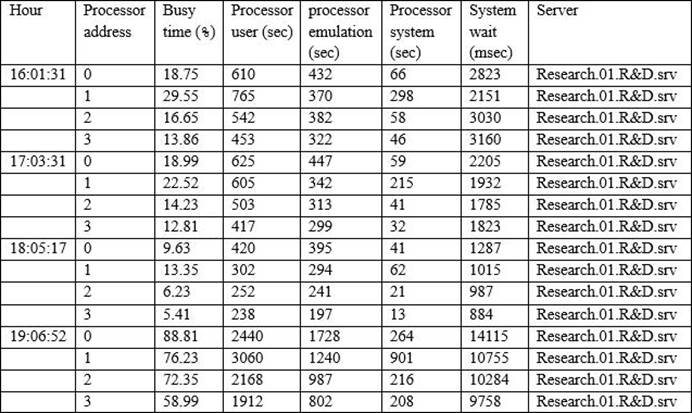
Which of the following actions should the security analyst take FIRST?
A . Initiate an investigation
B . Isolate the R&D server
C . Reimage the server
D . Determine availability
Answer: B