Posted by: Pdfprep
Post Date: January 13, 2021
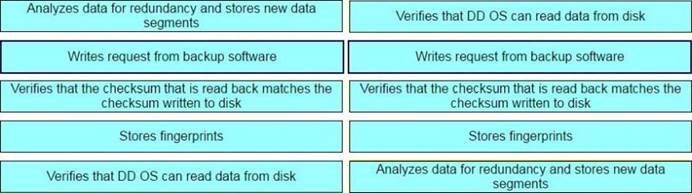
DRAG DROP
What is the correct sequence of operations used by the Dell EMC Data Domain Data Invulnerability Architecture (DIA) in the end-to-end verification process?
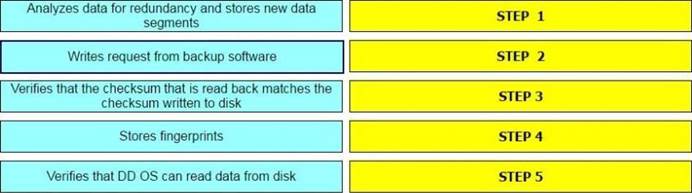
Answer: