(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.). Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal.
If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
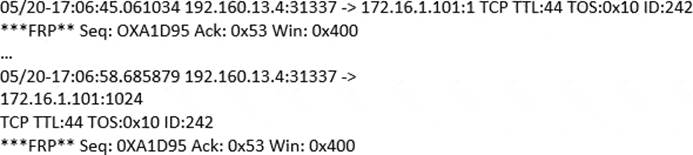
A . This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
B . This is back orifice activity as the scan comes from port 31337.
C . The attacker wants to avoid creating a sub-carries connection that is not normally valid.
D . These packets were crafted by a tool, they were not created by a standard IP stack.
Answer: B
