Refer to the exhibit.
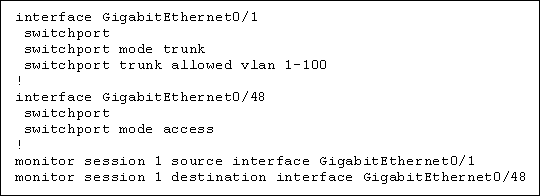
How can the traffic that is mirrored out the GigabitEthernet0/48 port be limited to only traffic that is received or transmitted in VLAN 10 on the GigabitEthernet0/1 port?
A . Change the configuration for GigabitEthernet0/48 so that it is a member of VLAN 10.
B . Add an access list to GigabitEthernet0/48 to filter out traffic that is not in VLAN 10.
C . Apply the monitor session filter globally to allow only traffic from VLAN 10.
D . Change the monitor session source to VLAN 10 instead of the physical interface.
Answer: C
Explanation:
To start a new flow-based SPAN (FSPAN) session or flow-based RSPAN (FRSPAN) source or destination session, or to limit (filter) SPAN source traffic to specific VLANs, use the monitor session filter global configuration command.
Usage Guidelines You can set a combined maximum of two local SPAN sessions and RSPAN source sessions. You can have a total of 66 SPAN and RSPAN sessions on a switch or switch stack. You can monitor traffic on a single VLAN or on a series or range of ports or VLANs. You select a series or range of VLANs by using the [ , | -] options. If you specify a series of VLANs, you must enter a space before and after the comma. If you specify a range of VLANs, you must enter a space before and after the hyphen ( -). VLAN filtering refers to analyzing network traffic on a selected set of VLANs on trunk source ports. By default, all VLANs are monitored on trunk source ports. You can use the monitor session session_number filter vlan vlan-id command to limit SPAN traffic on trunk source ports to only the specified VLANs. VLAN monitoring and VLAN filtering are mutually exclusive. If a VLAN is a source, VLAN filtering cannot be enabled. If VLAN filtering is configured, a VLAN cannot become a source. Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3850/software/release/3se/network_m anagement/command_reference/b_nm_3se_3850_cr/ b_nm_3se_3850_cr_chapter_010.html#wp3 875419997
