Posted by: Pdfprep
Post Date: May 22, 2021
A systems administrator is reviewing the following information from a compromised server:
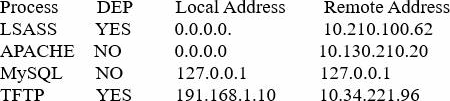
Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
A . Apache
B . LSASS
C . MySQL
D . TFTP
Answer: A
