Posted by: Pdfprep
Post Date: November 21, 2020
A security analyst is reviewing the following log after enabling key-based authentication.
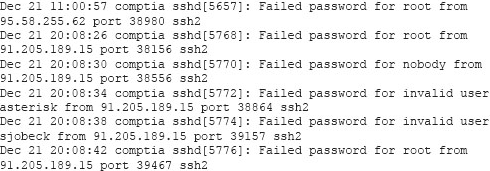
Given the above information, which of the following steps should be performed NEXT to secure the system?
A . Disable anonymous SSH logins.
B . Disable password authentication for SS
D . Disable SSHv1.
E . Disable remote root SSH logins.
Answer: B
