Posted by: Pdfprep
Post Date: November 14, 2020
A security administrator is implementing a new WAF solution and has placed some of the web servers behind the WAF, with the WAF set to audit mode.
When reviewing the audit logs of external requests and posts to the web servers, the administrator finds the following entry:
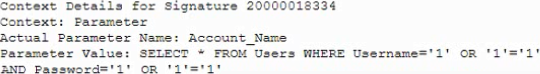
Based on this data, which of the following actions should the administrator take?
A . Alert the web server administrators to a misconfiguration
B . Create a blocking policy based on the parameter values
C . Change the parameter name ‘Account_Name’ identified in the log.
D . Create an alert to generate emails for abnormally high activity.
Answer: D

Leave a Reply