Posted by: Pdfprep
Post Date: November 6, 2020
A penetration tester is reviewing the following output from a wireless sniffer:
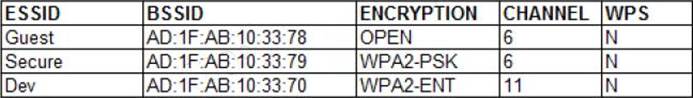
Which of the following can be extrapolated from the above information?
A . Hardware vendor
B . Channel interference
C . Usernames
D . Key strength
Answer: C
