HOTSPOT
You have an Azure subscription that contains the virtual machines shown in the following table.
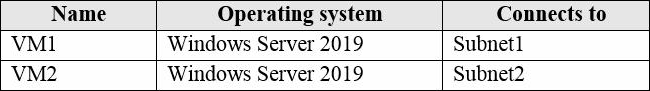
VM1 and VM2 use public IP addresses. From Windows Server 2019 on VM1 and VM2, you allow inbound Remote Desktop connections.
Subnet1 and Subnet2 are in a virtual network named VNET1.
The subscription contains two network security groups (NSGs) named NSG1 and NSG2.
NSG1 uses only the default rules.
NSG2 uses the default and the following custom incoming rule:
✑ Priority: 100
✑ Name: Rule1
✑ Port: 3389
✑ Protocol: TCP
✑ Source: Any
✑ Destination: Any
✑ Action: Allow
NSG1 connects to Subnet1. NSG2 connects to the network interface of VM2.
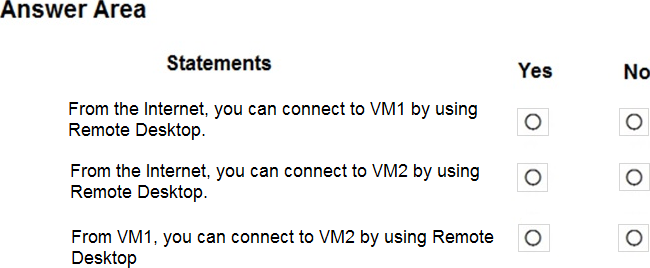
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Answer: 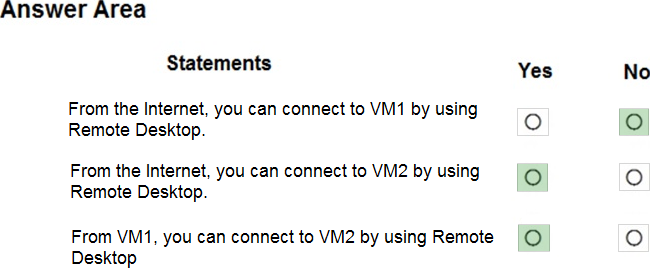
Explanation:
Box 1: No
The default port for RDP is TCP port 3389. A rule to permit RDP traffic must be created automatically when you create your VM.
Box 2: Yes
NSG2 will allow this.
Box 3: Yes
NSG2 will allow this.
Note on NSG-Subnet1: Azure routes network traffic between all subnets in a virtual network, by default.
References: https://docs.microsoft.com/en-us/azure/virtual-machines/troubleshooting/troubleshoot-rdp-connection

Leave a Reply